HIRE IOT SECURITY EXPERTS - PROFESSIONAL DEVICE PENETRATION TESTING
Need to hire IoT security specialists for smart device security testing? Our certified IoT penetration testers assess security vulnerabilities in connected devices, embedded systems, and industrial IoT infrastructure. When you need to hire ethical hackers for IoT security, trust professionals who understand hardware hacking, firmware analysis, and IoT protocols.
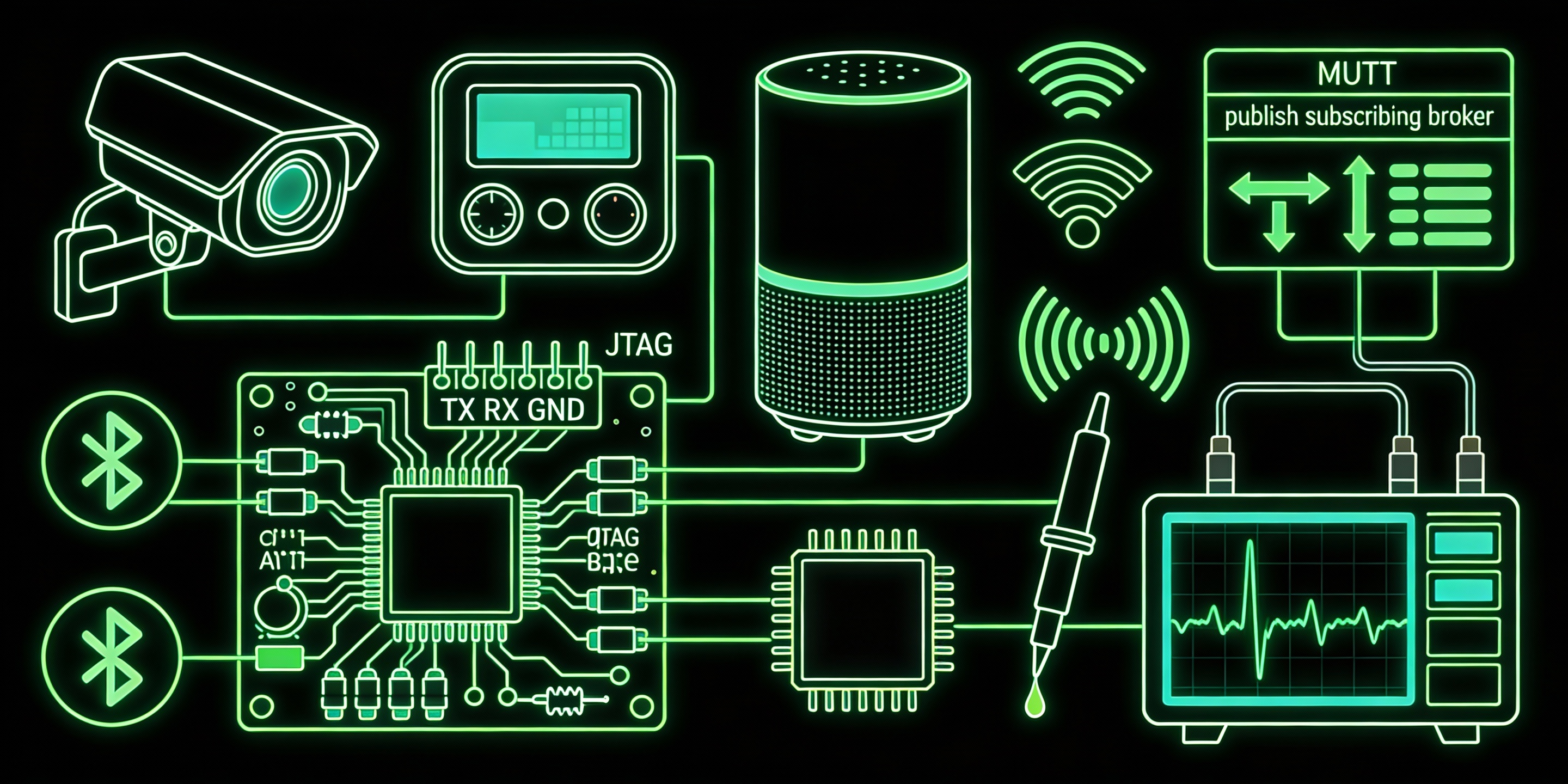
Looking to hire hackers for IoT device testing? We specialize in firmware extraction, UART/JTAG debugging, wireless protocol analysis (Zigbee, Z-Wave, BLE), and embedded device exploitation. Hire IoT security experts who deliver comprehensive assessments with proper authorization.