HIRE EXPLOIT DEVELOPERS - PROFESSIONAL ZERO-DAY RESEARCH
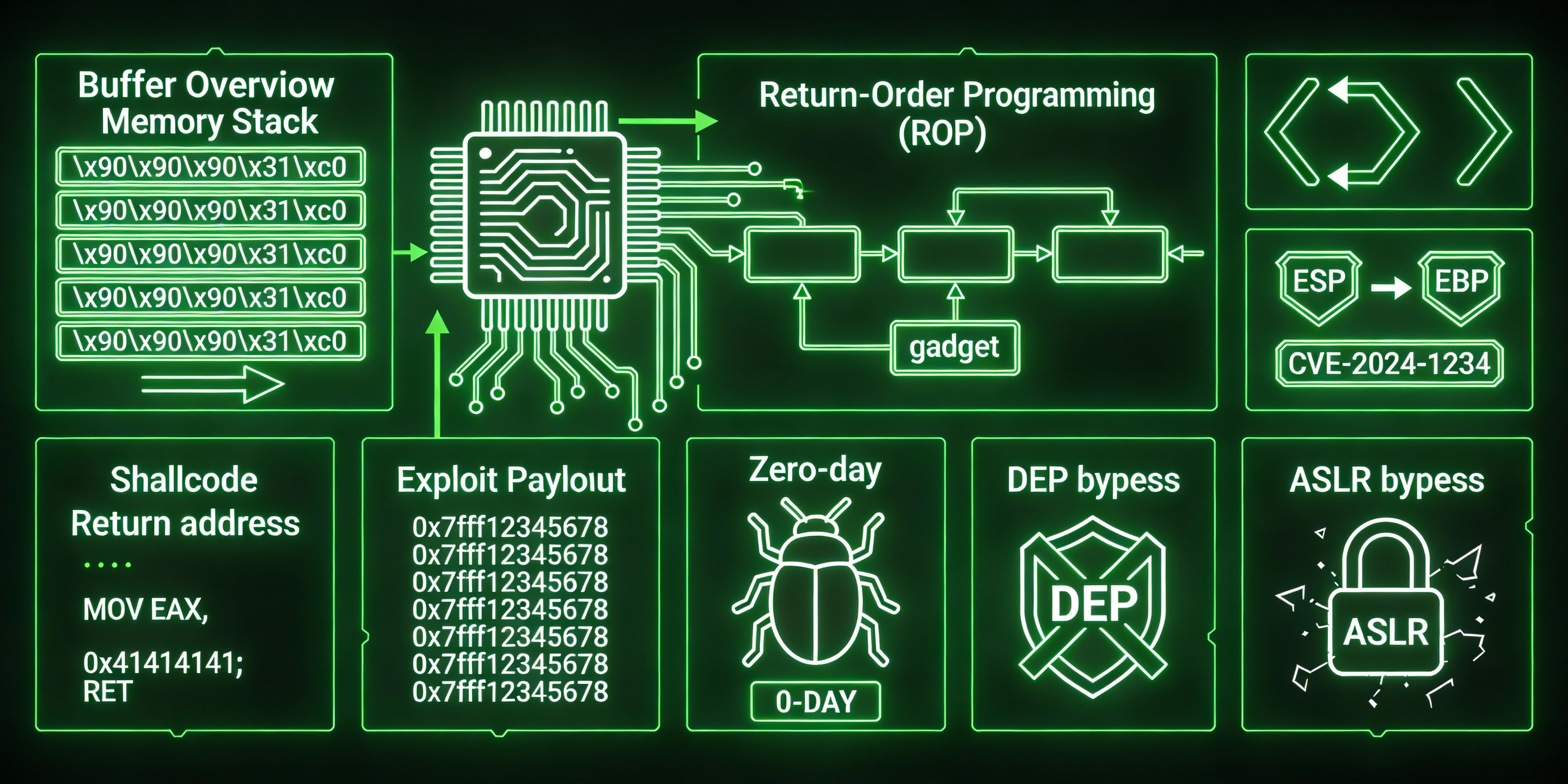
Need to hire exploit developers for vulnerability research and proof-of-concept development? Our certified exploit engineers specialize in memory corruption, ROP chains, heap exploitation, and modern bypass techniques. When you need to hire ethical hackers for exploit development, trust professionals with CVE credits and real-world experience.
Looking to hire hackers for zero-day research? We develop working exploits for buffer overflows, use-after-free bugs, and kernel vulnerabilities. Hire exploit development specialists who understand ASLR, DEP, and modern exploitation techniques for authorized security research.